Aircrack- ng]. This tutorial walks you through cracking WPA/WPA2 networks which use pre- shared keys. Crack WEP/WPA/WPA2 Password Without Dictionary/Bruteforce NEW. Crack WPA/WPA2 Wifi Password Without Dictionary/Brute Fore. Do WPA Dictionary Attacks. Capture the handshake Crack the handshake to get the password We have already covered WPA-handshake capture in a lot of detail. In this tutorial we will actually crack a WPA handshake file using dictionary attack. Our tool of choice for this tutorial will be aircrack-ng. We will not bother about the.
Getting a WPA or WPA2 handshake is great but what do you do once you have finally gotten one? Well it needs to be cracked. Unlike WEP, WPA/WPA2 is hard to crack and is usually done with Brute Force.
There are other ways such as Rainbow Tables and the video card attack, but the simplest or easiest way to crack WPA is to use Brute Force. The way this works basically is that there is a large dictionary that you use to throw as many combinations of words as possible at the WPA encryption until it cracks. If the password is easy then it will find it quick, if it is a long paraphrase with many different number letter combinations then it will be much harder.
Getting a good dictionary can be hard there are some dictionaries within Backtrack 5 that I will use to explain the Brute Force method but there size is limited making them useless against all but the easiest paraphrase.
Below I will show what I have in a video. if needed you can copy and past the code just be sure what files will need to be renamed such as the WPA/WPA2 capture itself.
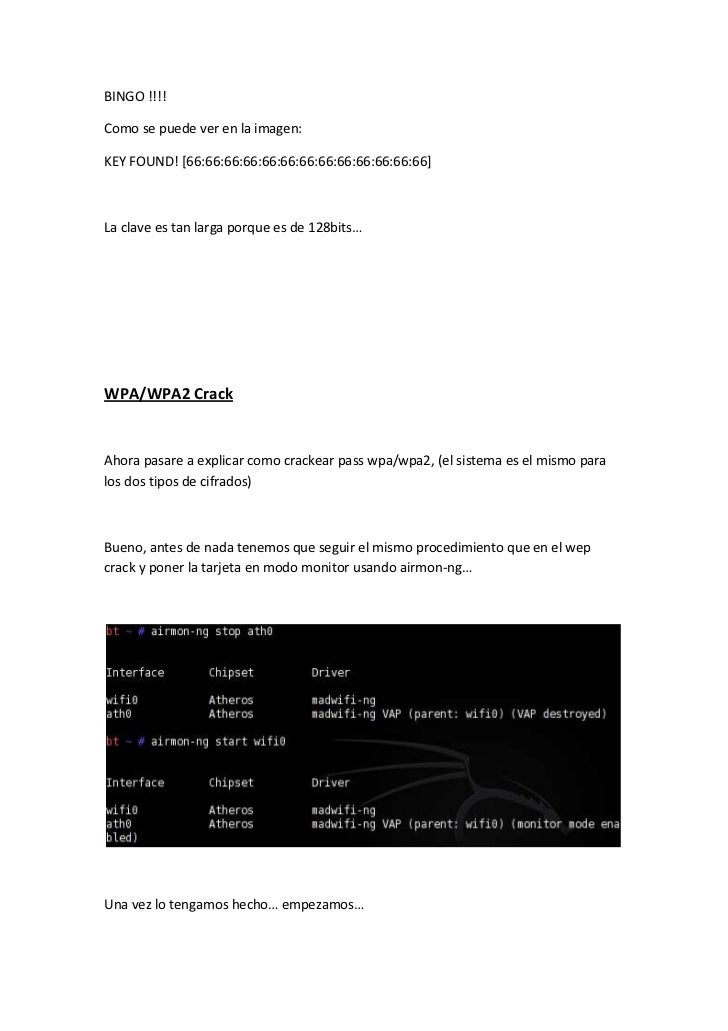
You should already have a WPA handshake file and Backtrack 5 running.
The default storage for a WPA handshake is under /root and will be there under what ever name you called it. The dictionary that we will use is built into backtrack under the /pentest/passwords/wordlists and is called darkc0de.lst.
(Be sure to use the number 0 in darkc0de.lst)
We will be using aircrack to do the cracking and the command to do this is:
aircrack-ng (file name) -w (dictionary location)
Where the file name is the handshake file you captured and the dictionary location is the path to your dictionary. The location of where this two files are and there names will be up to you. as I said above the usual default location of the handshake file is under /root and is what ever you called it. we will be using the darkc0de.lst dictionary for this example under the
/pentest/passwords/wordlists directory.
So the command for me to do this would be:
Crack Wpa Kali
aircrack-ng /root/mywpacatch-05.cap -w /pentest/passwords/wordlists/darkc0de.lst
If done right aircrack should start and begin to try to crack the WPA handshake capture with the dictionary.
If the dictionary finds it it will show as below if not then another dictionary will need to be used.
Join GitHub today
GitHub is home to over 40 million developers working together to host and review code, manage projects, and build software together.
Free Dictionary Download For Pc
 Sign up
Sign upHave a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Comments
commented Mar 23, 2015
Original issue reported on code.google.com by |
commented Mar 23, 2015
Original comment by |